The German Minister of the Interior, Mr. Zimmermann, just couldn’t believe it. There were really “adult judges” who adopted the “marginal concerns” of a radical minority against the census. And worse: only months later, constitutional judges formulated in a landmark decision what would prove to be visionary in the long run:
“Under the modern conditions of data processing, the free development of personality presupposes the protection of the individual against unlimited collection, storage, use and disclosure of his or her personal data. (…) In this respect, the fundamental right guarantees the right of the individual to determine the disclosure and use of his or her personal data on his or her own.”
From the census decision of the Federal Constitutional Court, December 1983
But who would have thought in those days that we would one day live in a world in which people would unlimitedly make their data available themselves? Which wouldn’t be a problem if it weren’t personal data. As soon as data can be traced back to a person, the interest in profiling begins to grow. The difficulty of effectively anonymizing data and the lack of awareness of why one should protect one’s identity is one reason why the Internet could be described as “broken”. It’s time to fix it and reinvent the wheel that’s rolling over us.
Digital self-determination stands and falls with the concept of identity
How do we verify an identity? Our everyday proof of identity functions via a marker that is as unique as possible: name, mobile number, passport, a signature, a familiar face. How unique and verifiable these markers must be, depends on the requirements. At the airport, of course, they are more strict than in the coffee shop on the corner.
Increasingly, we are also clearly recognizable for computers. Our mobile phone scans our fingerprint to unlock. At authorities or in hospitals, in everyday contracts or customer relationships — everywhere it is interesting to know exactly who is who. This creates trust or entitles you to benefits. And while we are there, we increasingly (and often carelessly) link our digital self with all kinds of features. For example, many people log on to websites with their Facebook account. Others use a health app.
Clothing sizes, creditworthiness, daily traffic routes, search queries — all this helps the algorithms to make us personalized offers or predict our behavior. From the data points that we leave behind on an hourly basis, omniscient computers could calculate an extremely comprehensive model of our characteristics, preferences and habits.
They could? They are actually doing it, since quite some time. At least, as long as we tell them who we are.
The only way to escape this system so was to avoid these conjunctions, e.g. keep away from social media, use discrete browsers and exercise data minimizastion. With increasing linkage, this idea is just doesn’t apply any more. This creates a great demand in techniques that enable us to prove our identity selectively and reliably without becoming highly profiled “transparent citizens”. There are promising approaches that are currently being developed and tested. One of the buzzwords is Self-Sovereign Identities (SSI).
Reclaiming the digital me
“Identity is at the core of each and every interaction. While the required level of trust between identities can vary from one interaction to another, the necessity to exchange it in a secure and privacy preserving manner is universal.”
The W3C and the Sovrin network and others are currently developing standards to create anonymous yet reliable interactions in the digital world. The basis for this should be a system of digital identity markers (“DID”) which are unique and eternally valid and can be created for each individual interaction. With the help of a key pair and a publicly accessible blockchain, it is possible to verify that the DID in question is authentic.
It does not matter if the issuer is the registry office or my grandmother. The occasion can be minor — there are enough DIDs for everyone. DIDs can say for example “This person …
- … is in our yoga studio customer no. 123 with a bonus credit.”
- … is our employee and is allowed to enter the house.”
- … has a press card.”
- … was vaccinated against measles.”
- … has a valid driving license and is over 21 years old.”
- … has paid for the book shipment XY and may receive the parcel.”
Linked, the information leads us to an increasingly complex picture of the person — separately, it only delivers the relevant information. The only thing that really matters is that the DID reliably guarantees the property in question. And not whether the other person is also interested in cats or dogs. At a bank, e.g., we can simply release exactly the set of information from our wallet that they really need. And they can verify this information absolutely reliably.
We must understand that anonymity is not for criminals, but the crucial building block for our free future
The term “anonymous” rises fears — and some politicians are doing their best to stir them up. Meanwhile, we have long since surrendered our digital sovereignty to dubious hands. Abuse of power comes as no surprise — The world’s governments as well as the overpowering Internet monopolies each pursue their own interests. A clear name obligation on Facebook, a state backdoor for news apps, Payback cards or the custom officers checking your Amazon account — we are slowly learning that being anonymous in cyberspace must not be the exception, but must become the rule.
So how are the requirements for advanced DID infrastructure formulated?
- It must be interoperable, i.e. open to everyone.
- It must be decentralised, not controlled by a single authority.
- It must be verifiable, i.e. incorruptible and always accessible for everyone.
- It must preserve the anonymity of the participants — only I control my wallet.
The Blockchain Bundesverband writes about this in its position paper:
“In the self-sovereign identity paradigm, individuals and entities are enabled to create and manage their identifiers in a decentralized fashion, without relying on a third-party identity provider. Unlike existing identity solutions that are structured from the perspective of the organization that provided an identifier, self-sovereign identities are structurally set out to work from the perspective of the individual or entity that is the subject of a given identifier.”
So, how does this thing work — and why only now?
Often, fast technical solutions have prevailed over sustainable ones. The issue of identity on the Internet was thought about early on, but it was only damage that made us wise. The blockchain has also spread surprisingly slowly as a technology (Bitcoin has been around for 10 years), but is now the basis of many digital practices such as smart contracts or auditing. Explaining self-sovereign identities in their entirety goes beyond the scope here (and others can do it better: here in brief and here in a longer keynote).
So here a brief summary of the essential points:
In contrast to “normally” assigned identity markers (passport, log-in etc.) or IDs managed by third parties (federated ID), Self-Sovereign Identity does not have a server controlled by anyone. All IDs are written into a blockchain which is shared between several servers (Distributed Ledger) and thus protected against individual manipulations. It is used to verify the DIDs which are being created in any number and anonymous using encryption. Nobody knows to whom a snippet of a blockchain is assigned, but everyone can check that it is there. There is no longer an opportunity to associate all the information about a person with each other. And all actors are just peers in a network accessible to all.
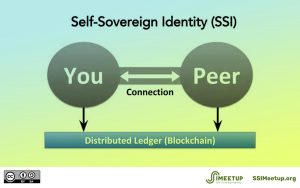
The principle of Self-Sovereign Identity is that both partners of the interaction are peers on a forgery-proof basis.
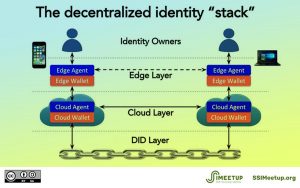
The principle of DID forms the basis for an infrastructure of anonymous but verifiable identity snippets.
DIDs are collected in digital wallets and transferred like passwords when needed — only they don’t have to be remembered. Apps, authorities, messenger services, social networks and anyone else can build their security architectures on this technical basis without having to fear manipulation. In this way, higher-level contracts can be addressed that take place on a different layer than the blockchain. This provides exactly the degree of anonymity or disclosure that both actors agree to. Monopolizing standards of state or private bodies become unnecessary.
The Pros — and cons?
The effects of such an infrastructure are incalculable. What Bitcoin is to the financial system — a currency whose rules are not controlled, but set in code — Self-Sovereign Identities can soon become to the rest of the digital cosmos. This toolbox moves the constitutionally guaranteed but lost informational self-determination back into the realm of the feasible. In the future, we will be more often free to decide in whom we trust. Which politician would not want to welcome and support this?
Well, it doesn’t take much imagination to think that Self-Sovereign Identities will not only have friends. Various actors profit from the traces that we leave in our technical communication and from which they form profiles. This includes marketing strategists as well as troll factories, the political or religious police in totalitarian states as well as the local criminal police, who now will have to come up with new methods. How could e.g. China maintain its policy of surveillance and popular education on this basis? Perhaps we will even see campaining against SSI or doubts being spread that the method really works.
Yet, a campaign against SSI would make just as little sense as a campaign against Bitcoin or the Darknet. Even the strongest actors are powerless against the development itself. Even influencing, e.g. by secret services, is unlikely to be successful in view of open source codes. And to which solutions citizens, entrepreneurs or consumers will turn in the end, is up to them.
//
Cartoon with kind permission of Ian Baker
Deepening links
Longer article on bitcoinblocks.net
New vokabulary to look up:
Anonymous Attribute Systems
Blockchain
Curated Identities
DDI (Decentralised Digital Identity)
DID = Decentralised Identifier (SSI stadard being developped by W3C)
DID Auth (SSI stadard on authetification being developped by DIF / IETF)
DKMS = interoperable key management (SSI stadard being developped by OASIS)
Digital Wallet
Distributed Ledgers
Etherium (blockchain application)
Federated identity
IAM (Identity and Access Management)
KNY (Know your customer)
PKI (Public Key Infrastructure)
Smart Contracts (technically applicable rules)
SSO (Single Sign-on)
SSI (Self-Sovereign Identities)
Token (transmitted valuable item)
Veryfiable Credentials (SSI stadard on verifiable credentials, being developped by W3C)